The way it is today, benefitting from the open environment of the internet also means constantly defending against hackers, malware, spam, and viruses. And unfortunately, no website, no matter the size, is insusceptible.
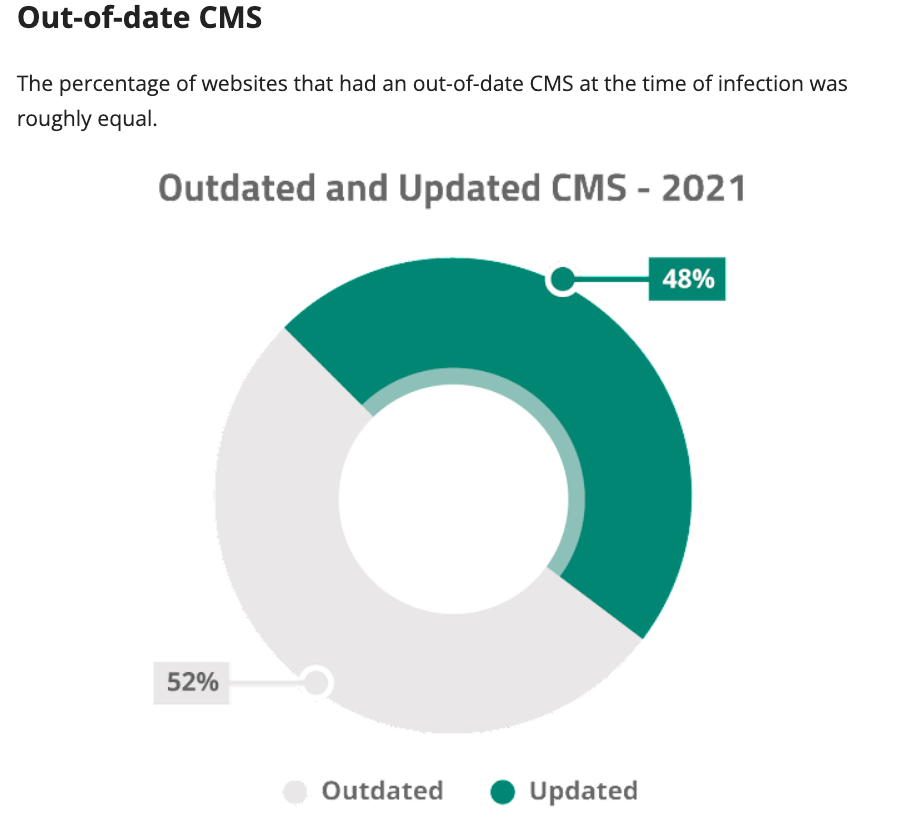
In years past, Google reported that over 50 million internet users have been warned about navigating to websites that pose a threat to their security. Sucuri, the security software company, reported that one of the most common causes of website hacking they found was out-of-date software, such as CMS.
Managing a dynamic, well-trafficked website requires constant evaluation and updates—maintaining a website is never a “one and done” type of task—but this applies to maintaining a secure website as well. For that reason, we recommend regularly updating your website security.
Is your site secure? How to prepare
There’s a sociological theory called the “Crime Opportunity Theory,” which basically says that if the risk is low and the reward is high, most people will take the chance to benefit from the opportunity. Here are the steps you can take, and absolutely should take, in order to protect your website from giving hackers that chance.
1. Keep up with security updates
All the core applications you use to power your website—your OS, database, PHP Apache web server, CMS platform, ecommerce platform—have security teams that release periodic security updates called “patches.” Security updates are released by each application to “patch” your website’s vulnerabilities as they’re uncovered by the security team, the developers, or even hackers.
You want to make sure to have a plan in place for staying on top of security updates. Once they’ve been released they reveal where weaknesses exist in your system.
We recommend that you set up a “patch rotation”—security update plan—with your internal IT team or an external web development team to keep your website up-to-date with new security patches as soon as they’re released.
Note: A quick word about the security of open-source platforms. Open-source software has quantifiably better security than closed-source platforms. Open-source platforms may give hackers access to the platform’s source code, but more importantly, they give access to the security teams on your side. Open-source provides a much broader group of developers access to update security, helping patches get released with more frequency.
2. Keep track of who’s doing what on your website
Enabling user accounts on your website is a good way to control who has access to what and track changes made by individual accounts. In general, the less access to your website’s back-end (the user interface administrators can access), the lower the “attack surface” your account represents to an attacker.
You should also “whitelist” usernames of valid admin, and not use common usernames like “admin” or “administrator.” Instead, use usernames that allow you to identify the specific people behind them. We recommend not having your co-workers share a single admin user account for that same reason.
Consider a more cautionary login process, like two-factor authentication which requires a one-time pin from your smartphone app (such as Google Authenticator) and changes every time you log in.
3. Don’t store valuable information on your website
Not all content is of equal value (to an attacker) on your website. Security for ecommerce and websites with user-generated content needs to be taken more seriously than general websites where your business is the only publisher of content. For ecommerce websites that store sensitive financial information, like credit card numbers, keeping your website PCI compliant is a good way to evaluate how secure your website is.
Payment Card Industry (PCI) Data Security Standard is a list of security standards managed and enforced by credit card brands. They’re tied to your merchant account and typically require quarterly compliance scans. Very few clients should consider holding credit card data. Instead, consider using a payment gateway or tokenized payment system, such as Authorize.net or Braintree. Or, completely offload the payment process to Amazon Payments or PayPal.
Note: Visit the PCI website for more information on compliance and how to make sure your website is up to PCI standards.
4. Configure webform submissions to send over TSL/SSL
We all use forms every day on the web to submit information via a website. Your website likely has many of them. Some of these are innocuous, signing up for an email newsletter. Others contain slightly more sensitive information, like your user login and password.
Forms are a favorite target for hackers, and there are many ways they can capture the data coming from those forms—assuming they’ve found access to do so. We recommend that you have your internal IT team or external developers configure your forms to be sent over TSL/SSL, the https:// protocol that encrypts data on the way to the server.
5. Make server adjustments
A server runs a collection of software (also called a “stack”) to let your user use your website. Each element of this stack, like the database that organizes your content, presents “attack surfaces.” Sooner or later, all elements of the stack are discovered to have a security flaw—sometimes minor, sometimes critical. Software is written by human beings, and unfortunately the more complex the component, the more prone it is to such vulnerabilities.
Making adjustments to the software run by your server and regularly checking its functionality is a good way to catch those inevitable security flaws. This is a more complex, technical task and will require IT.
6. Have a web application firewall
You’ve probably heard the term “firewall” before, but a web application firewall specifically acts as a barrier between your website and all web traffic, blocking suspicious-looking URLs, monitoring password attempts, and preventing malware installation. A WAF won’t catch everything and it’s not a complete solution to website security but it’s a strong deterrent to browsing, opportunistic hackers. There are numerous WAF software providers available, although we recommend Sucuri.
7. Defend against the rising threat of ransomware
An increasingly prevalent threat facing internet-facing applications is ransomware. This form of attack is a form of extortion whereby a hacker steals and/or corrupts your original data, encrypting the original version in such a way that it is no longer usable unless you pay a ransom—often in the form of cryptocurrency—in order for the hacker to return the original data to you, decrypted.
This type of attack works on the assumption that the original data is:
- Valuable to you in order to restore operations or recover from the impact on your business reputation.
- You are not able to restore the data. This is why having adequate backups, as per our point 7 above, can be vital—especially by ensuring that your backups are held 'offsite' in such a way that an attacker cannot access them in order to damage or encrypt your backups which would, again, elicit paying a ransom to recover.
- The attacker keeps their word by returning the original data to you after you pay (remember that there is little reason to believe a criminal's reassurances).
- Ransomware only works because organizations feel there is no other recourse with which to recover the data. Sometimes, an organization might recover the data themselves but still feel compelled to pay the ransom as a form of damage control if they believe that an attacker's leaking of the data will result in reputation harm. But there are no guarantees as to the outcome of having met an attacker's demands—the only guarantee is that you lose money.
For this reason, governments and law enforcement bodies are increasingly recommended not to pay ransoms either way. Some governments are even passing a law that forbids businesses from paying ransoms. The belief is that if organizations stop, or are even legally forbidden from paying ransoms, then this form of attack may become less lucrative for attackers, especially if the fines facing a business for having done so, are more expensive than the ransom demanded.
8. Phishing attacks
Security is an arms race, and with enough defenses such as firewalls, up-to-date software, the use of encryption of data in transit and at rest, and adequate monitoring, it becomes harder for attackers to use technical means to infect systems.
Behind every system, however, there are humans, and human nature remains fallible to other forms of attack which no amount of technology can prevent. As a result, attackers are increasingly relying on a technique known as 'phishing', which essentially involves tricking staff into performing some sort of action that effectively hands over access to an attacker without them even needing to exploit a technical software vulnerability.
Usually, this involves contacting the staff member while impersonating another staff member or manager, be it via e-mail, phone, or otherwise. The use of the LinkedIn network to identify and target new employees—preying on their inexperience at the organization—is a very common tactic.
You can defend against phishing by providing routine training to your staff to educate them on the nature of phishing, and how to identify a possible phishing scam attempt. You can also make use of some technology such as two-factor authentication so that accidental transmission of a password to an attacker is not sufficient for obtaining access.
Try to pursue a 'principle of least privilege', whereby your staff accounts in systems have the absolute minimum amount of permissions required for them to do their job. This can limit the amount of damage or 'pivoting' that an attacker can do, should they compromise a staff account.
9. Have a backup strategy
Even after doing everything you can to protect your website, something may go wrong. It may not be possible to repair damages or find an intruder’s entry point. In these circumstances, it’s good to have backups of your website’s information, in case you need to migrate everything to a new server installation. For every website we create, we have a daily (sometimes hourly) backup strategy of databases and entire disk images for rollback to prepare for these worst-case scenarios.
The best offense is a good defense
Most websites come under attack by opportunistic hackers looking for obvious system weaknesses to exploit. If you don’t give them one, and they don’t find one, generally they’ll move on looking for easier options.
Cybercrime is an unfortunate part of the reality of doing business online, and preparing for its eventuality is your best strategy, rather than waiting to deal with security breaches when they inevitably happen. New software is evolving constantly, and maintaining your website’s security to anticipate those developments should be a continuous effort.
